Threat Detection Software: A Deep Dive
CyberSecurity Insiders
APRIL 27, 2022
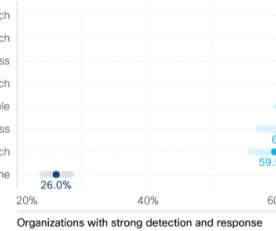
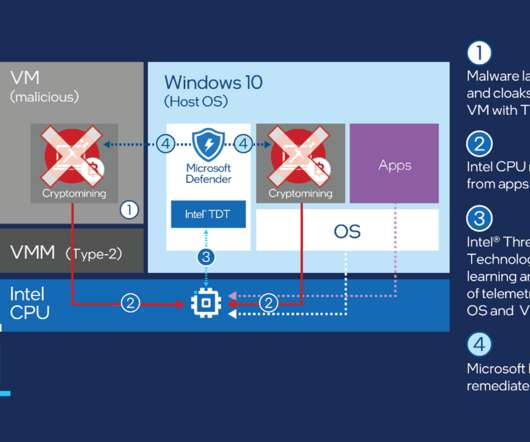
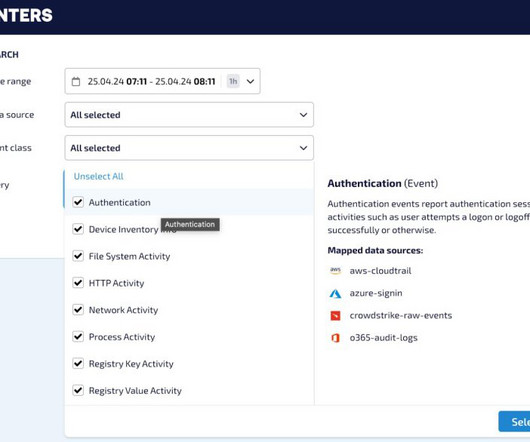
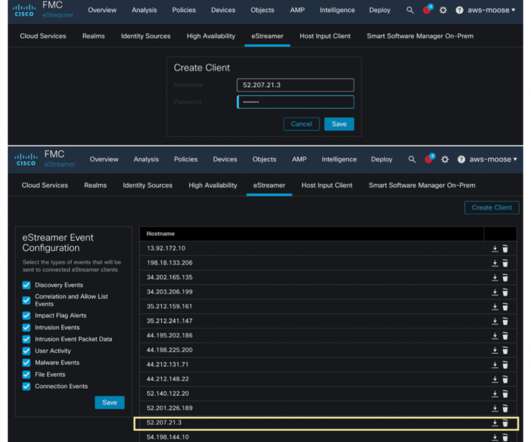
As the threat landscape evolves and multiplies with more advanced attacks than ever, defending against these modern cyber threats is a monumental challenge for almost any. Threat detection is about an organization’s ability to accurately identify threats, be it to. on your systems, threat detection is impossible.









































Let's personalize your content