IoT Unravelled Part 2: IP Addresses, Network, Zigbee, Custom Firmware and Soldering
Troy Hunt
NOVEMBER 23, 2020
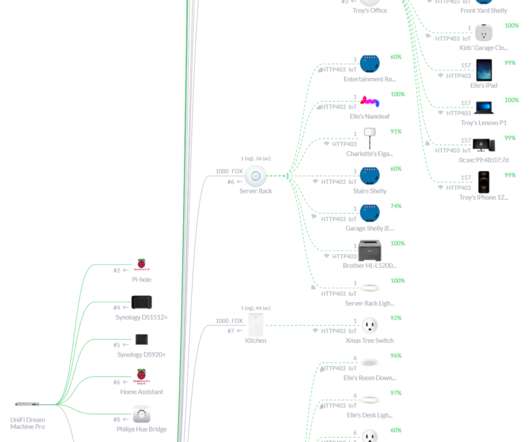
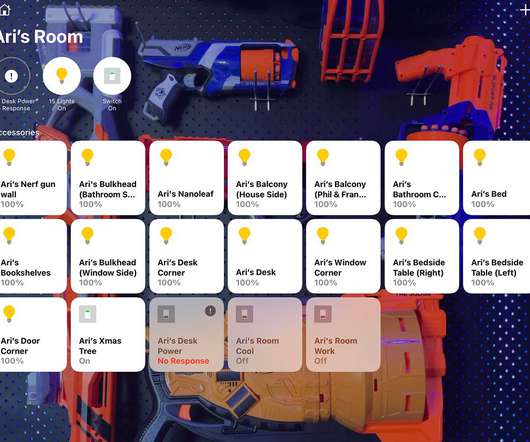
So, peeling back that next layer, the whole IoT space isn't just about devices that get their own IP address on your network and talk over TCP (or UDP). Let's drill into all that and then go deeper into custom firmware and soldering too. IoT and IP Addresses So, what happens when you start filling your home with IoT things?














































Let's personalize your content