Experts warn of anomalous spyware campaigns targeting industrial firms
Security Affairs
JANUARY 21, 2022
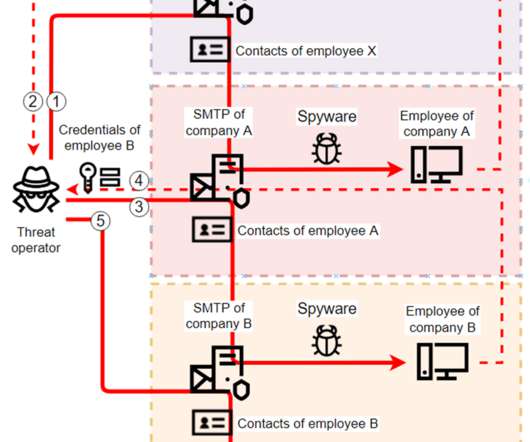
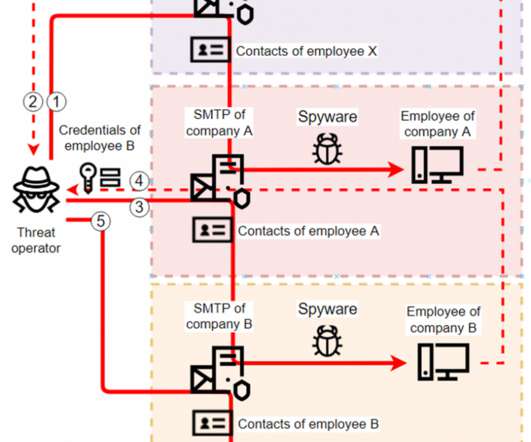
Researchers spotted several spyware campaigns targeting industrial enterprises to steal credentials and conduct financial fraud. Researchers from Kaspersky Lab have uncovered multiple spyware campaigns that target industrial firms to steal email account credentials and carry out fraudulent activities. ” concludes the report.


















Let's personalize your content