Hacking firm I-Soon data leak revealed Chinese gov hacking capabilities
Security Affairs
FEBRUARY 26, 2024
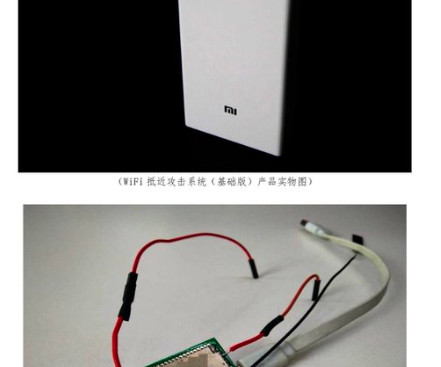
pic.twitter.com/ucfPwk7zi6 — 安坂星海 Azaka VTuber (@AzakaSekai_) February 18, 2024 Azaka noticed that the hacking firm has a DDoS system relying on a bot that can infect Windows, Linux, or generic IoT devices. The individuals responsible for the data theft and their motivations remain unknown.

















Let's personalize your content