Can smart cities be secured and trusted?
Thales Cloud Protection & Licensing
OCTOBER 15, 2019
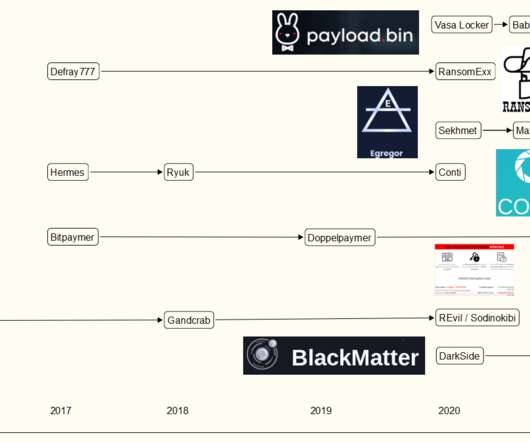
A report by US cyber-security firm Recorded Future published last May highlighted a spike in ransomware attacks targeting US cities. In June 2019, Riviera Beach in FL paid $600,000 to hackers to restore its email system and public records. The rapid hyper-connectivity and digitalization of cities are accelerating cyber threats.












Let's personalize your content