China-linked threat actors have breached telcos and network service providers
Security Affairs
JUNE 8, 2022
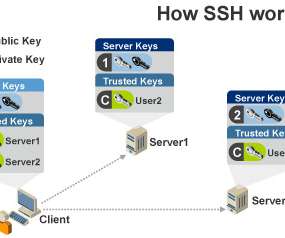
Ensure that you have dedicated management systems [ D3-PH ] and accounts for system administrators. sections “The Underdogs – Best Personal (non-commercial) Security Blog” and “The Tech Whizz – Best Technical Blog”). Protect these accounts with strict network policies [ D3-UAP ]. To nominate, please visit:?.



























Let's personalize your content