A Closer Look at the Snatch Data Ransom Group
Krebs on Security
SEPTEMBER 30, 2023
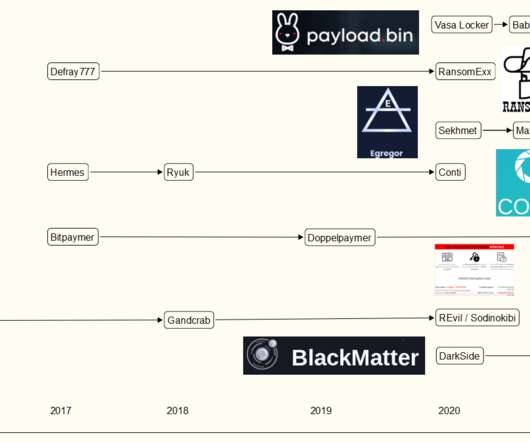
GandCrab dissolved in July 2019, and is thought to have become “ REvil ,” one of the most ruthless and rapacious Russian ransomware groups of all time. It continues: “Prior to deploying the ransomware, Snatch threat actors were observed spending up to three months on a victim’s system. .”














Let's personalize your content