A Closer Look at the Snatch Data Ransom Group
Krebs on Security
SEPTEMBER 30, 2023
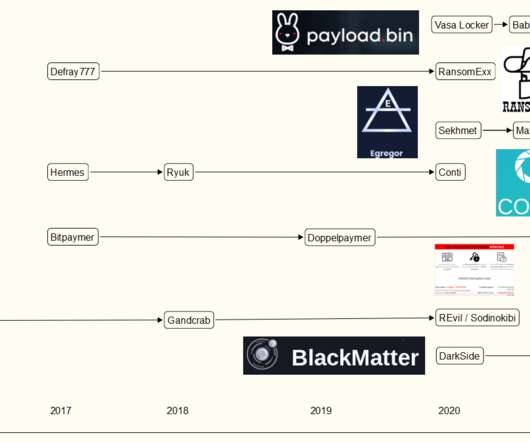
GandCrab dissolved in July 2019, and is thought to have become “ REvil ,” one of the most ruthless and rapacious Russian ransomware groups of all time. “The command requires Windows system administrators,” Truniger’s ads explained. “Experience in backup, increase privileges, mikicatz, network.















Let's personalize your content