Building a secure and scalable multi-cloud environment with Cisco Secure Firewall Threat Defense on Alkira Cloud
Cisco Security
FEBRUARY 2, 2023
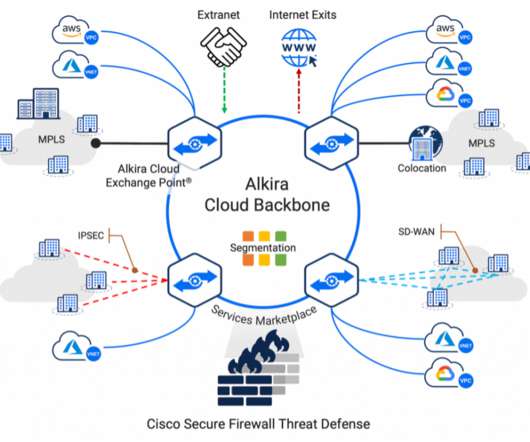
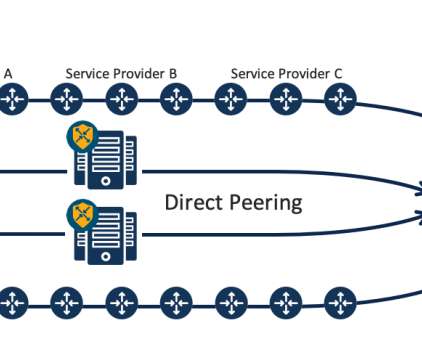
These applications/workloads move to, and reside in multi-cloud architecture, adding complexity to connectivity, visibility, and control. Secure Internet Edge: Deployment of Cisco Secure Firewall inside CXP enables secure Internet edge for inbound and outbound Internet traffic.












































Let's personalize your content