Building a Scalable Security Architecture on AWS with Cisco Secure Firewall and AWS Transit Gateway
Cisco Security
DECEMBER 13, 2021
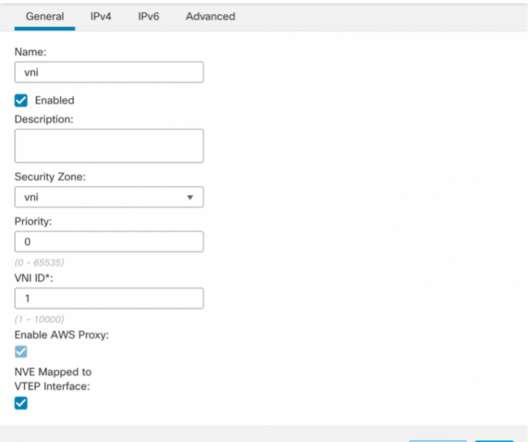
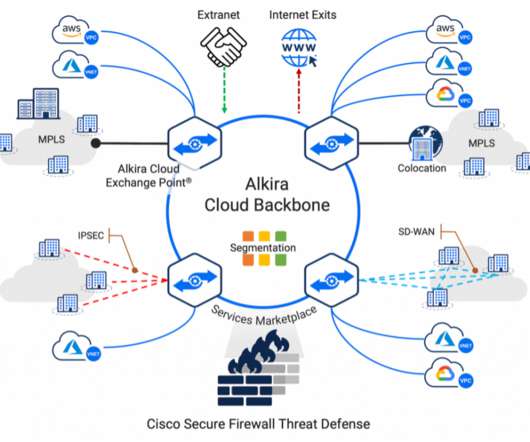
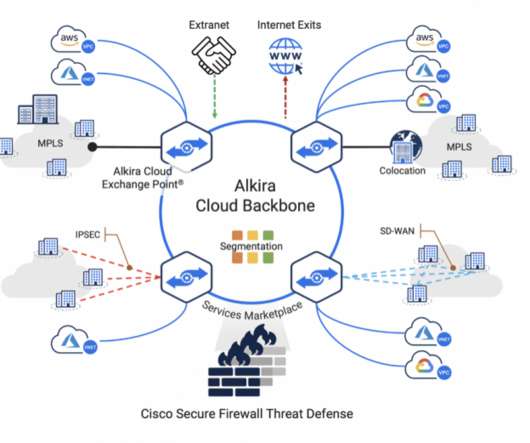
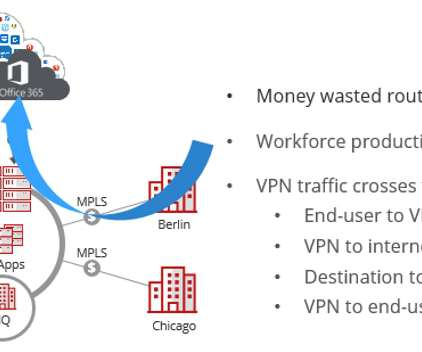
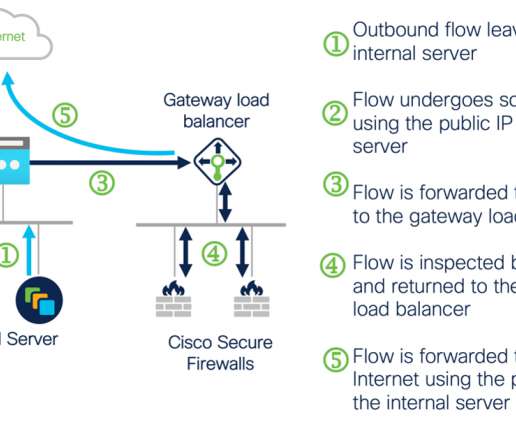
It makes architectures more scalable, in part by removing the need for source network address translation (SNAT) in the traffic path. Figure 1 below shows a scalable architecture for protecting ingress traffic using Cisco Secure Firewall and AWS Gateway Load Balancer. The workload sends traffic to the Internet.












































Let's personalize your content