Experts link Raspberry Robin Malware to Evil Corp cybercrime gang
Security Affairs
SEPTEMBER 2, 2022
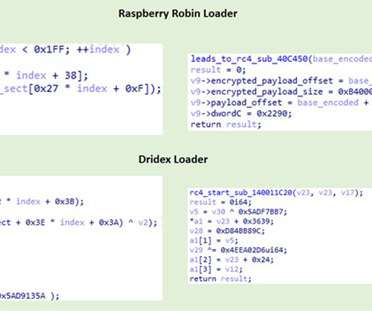
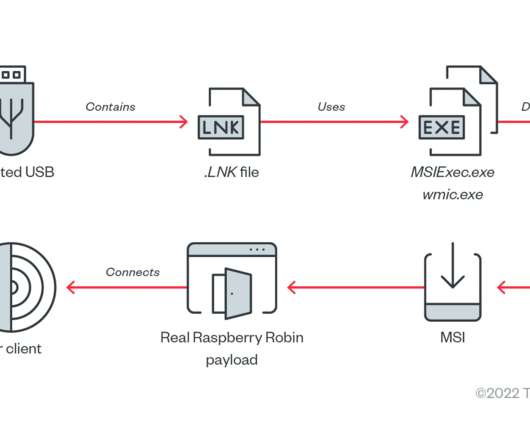
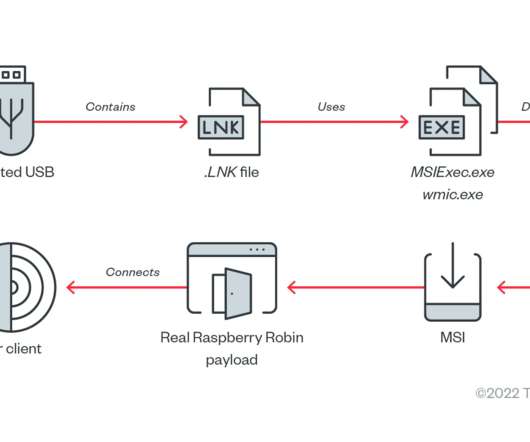
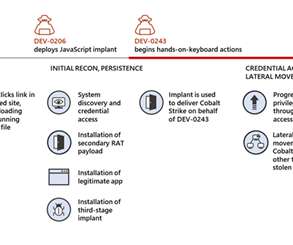
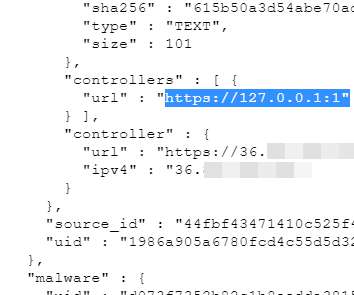
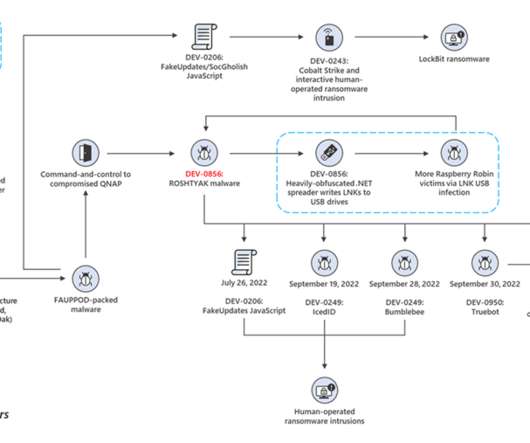
Researchers attribute the Raspberry Robin malware to the Russian cybercrime group known as Evil Corp group. IBM Security X-Force researchers discovered similarities between a component used in the Raspberry Robin malware and a Dridex malware loader, which was part of the malicious operations of the cybercrime gang Evil Corp.









































Let's personalize your content