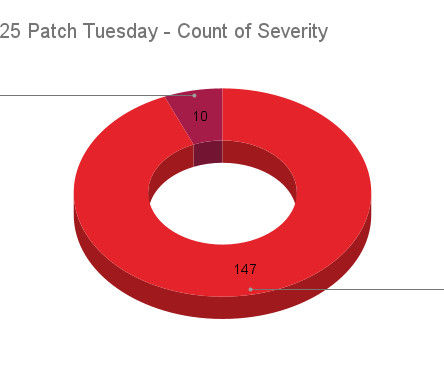
Microsoft: Happy 2025. Here’s 161 Security Updates
Krebs on Security
JANUARY 14, 2025
.” Bob Hopkins at Immersive Labs called attention to the CVE-2025-21311 , a 9.8 “critical” bug in Windows NTLMv1 (NT LAN Manager version 1), an older Microsoft authentication protocol that is still used by many organizations.
















Let's personalize your content