Perfectl Malware
Schneier on Security
OCTOBER 14, 2024
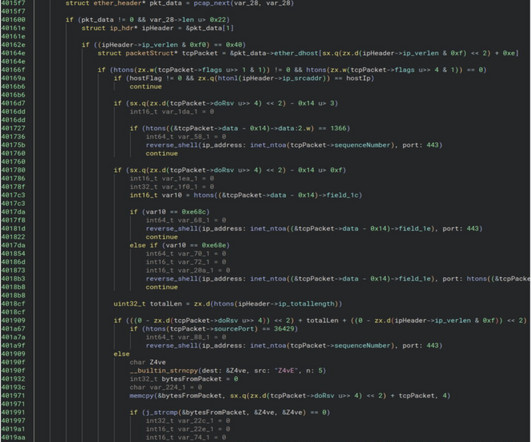
Perfectl in an impressive piece of malware: The malware has been circulating since at least 2021. The researchers are calling the malware Perfctl, the name of a malicious component that surreptitiously mines cryptocurrency. The naming convention is one of the many ways the malware attempts to escape notice of infected users.











Let's personalize your content