IoT Devices in Password-Spraying Botnet
Schneier on Security
NOVEMBER 6, 2024
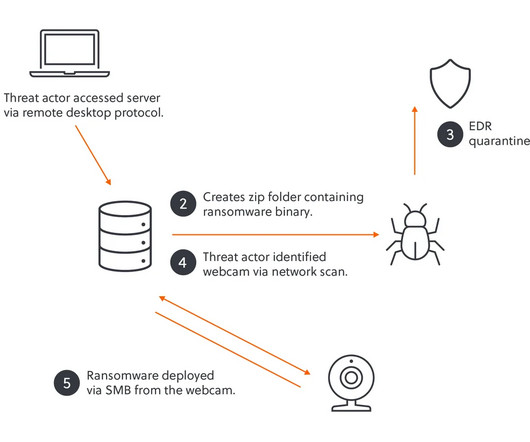
Microsoft is warning Azure cloud users that a Chinese controlled botnet is engaging in “highly evasive” password spraying. ” Some of the characteristics that make detection difficult are: The use of compromised SOHO IP addresses The use of a rotating set of IP addresses at any given time.















Let's personalize your content