How phishing attacks evade traditional security defenses
Tech Republic Security
MARCH 30, 2021
Two of three phishing pages analyzed by Armorblox were hosted on legitimate services to try to sneak past the usual security protection.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
 Security Defenses Related Topics
Security Defenses Related Topics 
Tech Republic Security
MARCH 30, 2021
Two of three phishing pages analyzed by Armorblox were hosted on legitimate services to try to sneak past the usual security protection.

The Hacker News
AUGUST 16, 2021
A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone, some of which have slipped past Apple's on-device malware scanner and even signed by its own notarization service, highlighting the malicious software ongoing attempts to adapt and evade detection.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Hacker News
MAY 21, 2024
Microsoft on Monday confirmed its plans to deprecate NT LAN Manager (NTLM) in Windows 11 in the second half of the year, as it announced a slew of new security measures to harden the widely-used desktop operating system.

Tech Republic Security
MARCH 11, 2020
A Trend Micro report finds that spammers are using public and hosted cloud infrastructure to slip malicious emails past security defenses.

Tech Republic Security
FEBRUARY 19, 2021
The Dark Web allows cybercriminals to create a Cyber Attacks-as-a-Service ecosystem that outmaneuvers security defenses. Here are tips on how businesses can try to thwart cybercrime.

Tech Republic Security
APRIL 14, 2022
Hackers are using a technique known as Quoted-printable to trick security defenses into thinking a malicious link is legitimate, says Avanan. The post How cybercriminals are creating malicious hyperlinks that bypass security software appeared first on TechRepublic.

The Hacker News
JUNE 25, 2024
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management Console (MMC) and evade security defenses.
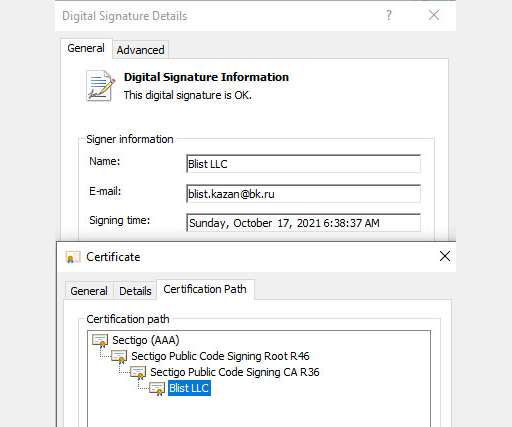
The Hacker News
DECEMBER 24, 2021
Cybersecurity researchers have disclosed details of an evasive malware campaign that makes use of valid code signing certificates to sneak past security defenses and stay under the radar with the goal of deploying Cobalt Strike and BitRAT payloads on compromised systems.

CSO Magazine
JULY 13, 2021
To protect your enterprise against security threats, you need maximum visibility. That’s the fundamental notion behind SIEM (security information and event management) software, which is essential to the security defenses of most large and many medium enterprises.

The Hacker News
SEPTEMBER 1, 2023
As cyber threats continue to evolve, adversaries are deploying a range of tools to breach security defenses and compromise sensitive data. This article explores the seriousness of compromised credentials, the challenges they present to security solutions, and the

Security Boulevard
FEBRUARY 28, 2021
Everyone knows that cybersecurity is a red-hot career field, and chief security officers (or chief information security officers in many organizations) are the ones leading the online security defense.

Schneier on Security
JUNE 15, 2020
In fact, the cyber operations budget is higher than the budgets for the CISA, the FBI and the Department of Justice's National Security Division combined ($3.7 government budgeted as much on military construction for cyber units as it did for the entirety of Homeland Security ($1.9 billion compared to $2.21 billion compared to $371.4

Security Boulevard
FEBRUARY 29, 2024
As today’s security threat environment evolves, SaaS security posture management (SSPM) has become a key part of a CISO's security defense plan. The post A CISO’s Guide to SaaS Security Posture Management appeared first on Security Boulevard.

CyberSecurity Insiders
DECEMBER 27, 2021
As some hackers have developed a malware that uses code signing certificates to avoid detection by security defenses and has the tendency to download payloads onto a compromised system.

Security Boulevard
JUNE 8, 2023
Arguably, security defenses and awareness still lag behind the pace of digital transformation in manufacturing, where informational and operational. Read More The post Cybersecurity in Manufacturing: Key Threats and Risks appeared first on Nuspire.
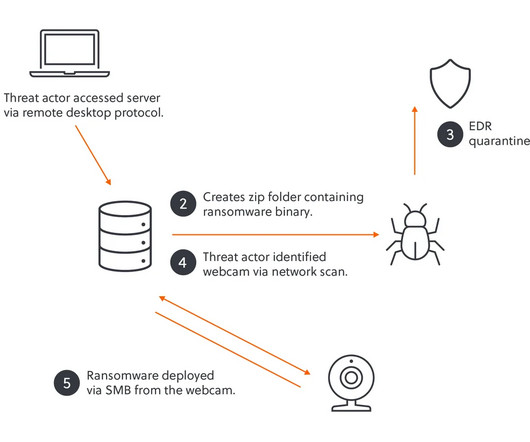
Security Affairs
MARCH 8, 2025
They found unsecured IoT devices, including webcams and a fingerprint scanner, using them to bypass security defenses and successfully deploy the ransomware. Realizing EDR was active, they pivoted by scanning the network for vulnerable devices.

Security Affairs
OCTOBER 17, 2022
Black Lotus is able to disable security solutions, including Hypervisor-protected Code Integrity (HVCI), BitLocker, and Windows Defender. The rootkit is able to bypass security defenses like UAC and Secure Boot, it is able to load unsigned drivers used to perform a broad range of malicious activities.

Security Boulevard
JULY 23, 2024
Security experts and government bodies have strongly advocated for companies adopting multifactor authentication (MFA) in recent years. But despite the increased adoption of MFA, security defenses don’t seem to be bolstered against rampant ransomware actors. In fact, recent findings suggest an increase in ransomware losses.

Krebs on Security
MAY 17, 2022
“From the details you offered, issue may probably caused by your computer security defense system as it seems not recognized our rarely used driver & detected it as malicious or a virus,” Saicoo’s support team wrote in an email. “When driver installed, this message will vanish out of sight.

Security Affairs
AUGUST 6, 2021
The company confirmed the security breach and launched an investigation into the incident with the help of external security experts. “GIGABYTE, a major manufacturer of motherboards and graphics cards, confirmed that some servers were attacked by hackers today, and the security defense was activated as soon as possible.

Security Affairs
SEPTEMBER 11, 2024
. “ RansomHub used TDSSKiller with the -dcsvc flag to try disabling critical security services, specifically targeting Malwarebytes Anti-Malware Service (MBAMService). The command aimed to disrupt security defenses by disabling this service. In this instance, attackers attempted to disable MBAMService.
Security Boulevard
OCTOBER 15, 2024
With the rapid growth of the internet, especially in areas like cloud computing, 5G, and IoT technologies, the scale of botnets continues to expand, intensifying the battle between attack and defense. In response, DDoS attacks have evolved, taking on a more intelligent form to evade security defenses.

Schneier on Security
APRIL 26, 2021
The inherent ambiguity in most other systems ends up being a near-term security defense against AI hacking. This is why most of the current examples of goal and reward hacking come from simulated environments. These are artificial and constrained, with all of the rules specified to the AI.

eSecurity Planet
FEBRUARY 26, 2025
As businesses rely more on mobile devices for authentication and communication, these evolving threats are slipping past conventional security defenses, putting corporate networks at greater risk. Zimperium found that mishing activity peaked in August 2024, with over 1,000 daily attacks recorded. What is mishing?

Krebs on Security
SEPTEMBER 14, 2022
As more governments and repressive entities around the world have begun purchasing powerful commodity spyware to target individuals of particular importance or interest, iOS’s general security defenses haven’t been able to keep pace with these specialized threats.”

Cisco Security
AUGUST 17, 2021
Email Attachments: One of two main methods to penetrate security defenses with malicious content by email. However, the use of emerging technologies has exploded, given the growth of AI-driven capabilities to identify good to malicious emails.

IT Security Guru
DECEMBER 15, 2022
By shifting security professionals’ mindset from a disparate, tool-based approach to a platform approach, businesses can improve their identity security defenses to protect against the modern threat landscape.” .

Krebs on Security
JULY 8, 2019
But GandCrab far eclipsed the success of competing ransomware affiliate programs largely because its authors worked assiduously to update the malware so that it could evade antivirus and other security defenses. in , where the group recruited many of its distributors.

Hacker Combat
JUNE 2, 2022
After a severe ransomware assault has hit them, they devote the necessary time and money to strengthening their cyber security defenses. Unfortunately, many businesses do not take this issue seriously. Since prevention is better than cure, it is essential not to wait until It’s too late to take precautionary measures.

eSecurity Planet
SEPTEMBER 21, 2023
See the Top Cybersecurity Companies Get the Free Cybersecurity Newsletter Strengthen your organization's IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices. Email Address By signing up to receive our newsletter, you agree to our Terms of Use and Privacy Policy.

CyberSecurity Insiders
OCTOBER 11, 2022
Through ongoing risk-based vulnerability assessments, you can continually evaluate the strength of your security defenses and promptly detect cracks in the armor – on the human, network, application, and systems fronts. This helps you identify logical flaws, misconfigurations, and unknown vulnerabilities that scanners may miss.

eSecurity Planet
SEPTEMBER 9, 2022
Healthcare Security Defenses. Two of the more common healthcare cybersecurity defenses the report found are training and awareness programs and employee monitoring.

Webroot
APRIL 4, 2022
“With security risks escalating worldwide and a persistent state of ‘unprecedented’ threats, compromises are inevitable. This year’s findings reiterate the need for organizations to deploy strong multi-layered security defenses to help them remain at the heart of cyber resilience and circumvent even the most creative cybercriminals.”.

eSecurity Planet
NOVEMBER 17, 2022
The conference’s focus on cyber resilience doesn’t mean that organizations should abandon core security defenses like EDR , access control and firewalls , but they should be prepared for the advanced threats that will, at some point, get past them.

The Last Watchdog
MAY 17, 2021
We are in the early stages of repurposing legacy security systems, and, ultimately replacing them, with security defenses that are every bit as agile as legit digital commerce has become. It’s encouraging that smarter security frameworks like CWPP and CSPM are coalescing; they signal the direction we need to keep heading in.

eSecurity Planet
JANUARY 29, 2024
Get Free Dashlane Access Get the Free Cybersecurity Newsletter Strengthen your organization's IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices. Email Address By signing up to receive our newsletter, you agree to our Terms of Use and Privacy Policy.

Hacker Combat
APRIL 6, 2022
The best ransomware protection combines solid, layered security defenses with data backups that an attacker can’t encrypt. Backing up your data ensures you do not get hit by an attack, or if it happens, you won’t lose any critical data. Regular Software Updates.

SecureWorld News
JULY 29, 2024
government, Leidos handles sensitive information related to national security, defense, and various federal operations. The exposure of internal documents could have serious ramifications, potentially compromising national security and the integrity of government operations. As a significant IT services provider to the U.S.

Security Affairs
APRIL 10, 2023
The attackers were able to interfere with security tools using Group Policy Objects (GPO). Once bypassed the security defenses, the attackers deployed the ransomware payload in the NETLOGON shares on several domain controllers. Then the attackers maintain persistence by registering a scheduled task using GPO.

eSecurity Planet
AUGUST 8, 2023
Read next: Top Enterprise Encryption Products Top Cybersecurity Startups Get the Free Cybersecurity Newsletter Strengthen your organization's IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices.

eSecurity Planet
SEPTEMBER 13, 2023
. “Additionally, it’s important to have an incident response plan in place to swiftly detect and mitigate any security breaches to minimize the potential impact.” Email Address By signing up to receive our newsletter, you agree to our Terms of Use and Privacy Policy.

Security Affairs
NOVEMBER 3, 2022
In order to weaken the security defenses installed on the target machine, Black Basta targets installed security solutions with specific batch scripts downloaded into the Windows directory. The threat actors were disabling Windows Defender executing the following scripts: WindowsILUg69ql1.bat bat WindowsILUg69ql2.bat

Security Affairs
MARCH 5, 2025
Microsoft has notified affected customers and is raising awareness to help mitigate Silk Typhoons threats, offering guidance to disrupt their operations and enhance security defenses. The group has been active since at least 2020, they use web shells for command execution and data theft.

eSecurity Planet
AUGUST 21, 2023
Last week’s major vulnerabilities: Weekly Vulnerability Recap – August 14, 2023 – Old or New, Vulnerabilities Need Management Get the Free Cybersecurity Newsletter Strengthen your organization's IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content