T-Mobile Data Breach
Schneier on Security
AUGUST 19, 2021
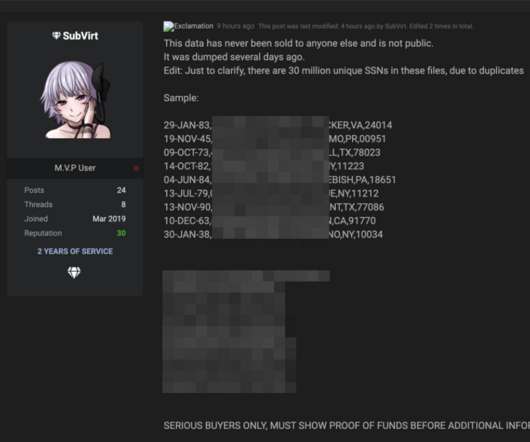
It’s a big one : As first reported by Motherboard on Sunday, someone on the dark web claims to have obtained the data of 100 million from T-Mobile’s servers and is selling a portion of it on an underground forum for 6 bitcoin, about $280,000.


















Let's personalize your content