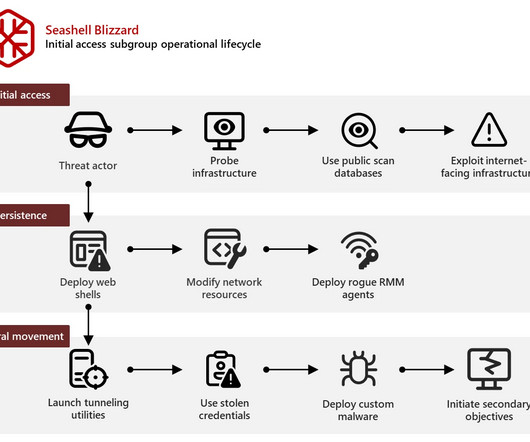
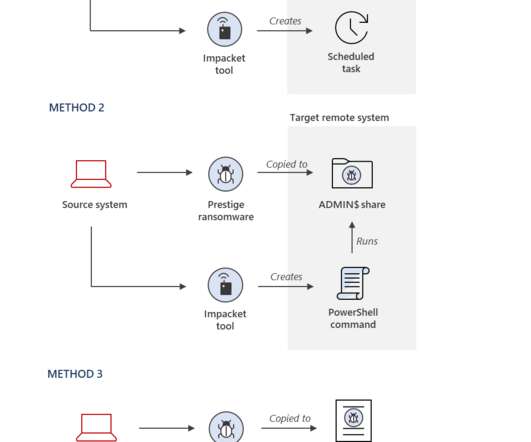
Russia-linked APT Seashell Blizzard is behind the long running global access operation BadPilot campaign
Security Affairs
FEBRUARY 13, 2025
Seashell Blizzard (aka Sandworm , BlackEnergy and TeleBots ) has been active since 2000, it operates under the control of Unit 74455 of the Russian GRUs Main Center for Special Technologies (GTsST). On September 2022, the Sandworm group was observed impersonating telecommunication providers to target Ukrainian entities with malware.









Let's personalize your content