LockBit Ransomware operators hit Swiss helicopter maker Kopter
Security Affairs
DECEMBER 6, 2020
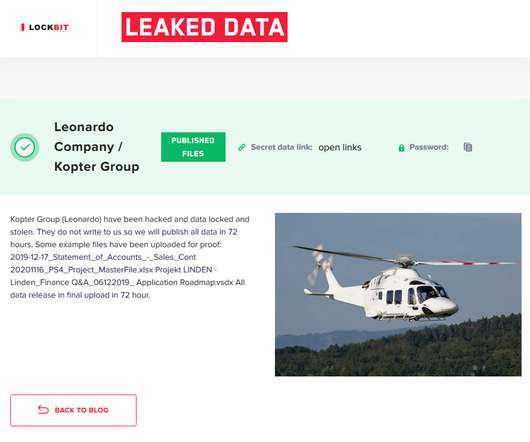
LockBit ransomware operators have compromised the systems at the helicopter maker Kopter and published them on their darkweb leak site. The helicopter maker Kopter was hit by LockBit ransomware, the attackers compromised its internal network and encrypted the company’s files. SecurityAffairs – hacking, ransomware).









Let's personalize your content