National Cyber Security Centre Study: Generative AI May Increase Global Ransomware Threat
Tech Republic Security
JANUARY 24, 2024
See the National Cyber Security Centre's predictions for generative AI for cyber attack and defense through 2025.

Tech Republic Security
JANUARY 24, 2024
See the National Cyber Security Centre's predictions for generative AI for cyber attack and defense through 2025.

Schneier on Security
JANUARY 4, 2024
Kaspersky researchers are detailing “an attack that over four years backdoored dozens if not thousands of iPhones, many of which belonged to employees of Moscow-based security firm Kaspersky.” It’s a zero-click exploit that makes use of four iPhone zero-days. The most intriguing new detail is the targeting of the heretofore-unknown hardware feature, which proved to be pivotal to the Operation Triangulation campaign.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
JANUARY 22, 2024
Leaked records reveal what appears to be the first known instance of a police department attempting to use facial recognition on a face generated from crime-scene DNA. It likely won’t be the last.

Troy Hunt
JANUARY 17, 2024
It feels like not a week goes by without someone sending me yet another credential stuffing list. It's usually something to the effect of "hey, have you seen the Spotify breach", to which I politely reply with a link to my old No, Spotify Wasn't Hacked blog post (it's just the output of a small set of credentials successfully tested against their service), and we all move on.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Krebs on Security
JANUARY 30, 2024
On Jan. 9, 2024, U.S. authorities arrested a 19-year-old Florida man charged with wire fraud, aggravated identity theft, and conspiring with others to use SIM-swapping to steal cryptocurrency. Sources close to the investigation tell KrebsOnSecurity the accused was a key member of a criminal hacking group blamed for a string of cyber intrusions at major U.S. technology companies during the summer of 2022.

Joseph Steinberg
JANUARY 10, 2024
Cybersecurity For Dummies , the best-selling cybersecurity book written for general audiences by Joseph Steinberg , is now available in Portuguese. Like its English, French, Dutch, and German counterparts, the Portuguese edition, entitled Cibersegurança Para Leigos , and published in Brazil, helps people stay cyber-secure regardless of their technical skillsets.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Schneier on Security
JANUARY 17, 2024
Interesting research: “ Do Users Write More Insecure Code with AI Assistants? “: Abstract: We conduct the first large-scale user study examining how users interact with an AI Code assistant to solve a variety of security related tasks across different programming languages. Overall, we find that participants who had access to an AI assistant based on OpenAI’s codex-davinci-002 model wrote significantly less secure code than those without access.

Lohrman on Security
JANUARY 21, 2024
The 54th Annual Meeting of The World Economic Forum took place in Davos, Switzerland, this past week, and cybersecurity and AI were again top topics. Here are some highlights.

Troy Hunt
JANUARY 29, 2024
I've always thought of it a bit like baseball cards; a kid has a card of this one player that another kid is keen on, and that kid has a card the first one wants so they make a trade. They both have a bunch of cards they've collected over time and by virtue of existing in the same social circles, trades are frequent, and cards flow back and forth on a regular basis.

Krebs on Security
JANUARY 10, 2024
A California man who lost $100,000 in a 2021 SIM-swapping attack is suing the unknown holder of a cryptocurrency wallet that harbors his stolen funds. The case is thought to be first in which a federal court has recognized the use of information included in a bitcoin transaction — such as a link to a civil claim filed in federal court — as reasonably likely to provide notice of the lawsuit to the defendant.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Joseph Steinberg
JANUARY 18, 2024
Over the past year I have experimented to see how various retailers handle personal information that they collect from customers, especially when such information is collected as part of a purchase made by the customer in what appears, at first glance, to be some “amazing deal.” As I have warned for decades, just as they are in the physical world, “too good to be true” prices found online are often scams; one should be especially careful when dealing with retailers who advertise such prices but

Tech Republic Security
JANUARY 31, 2024
Cyber threat hunting is the proactive process of searching for and detecting potential threats or malicious activities within a network or system.

Schneier on Security
JANUARY 24, 2024
New research into poisoning AI models : The researchers first trained the AI models using supervised learning and then used additional “safety training” methods, including more supervised learning, reinforcement learning, and adversarial training. After this, they checked if the AI still had hidden behaviors. They found that with specific prompts, the AI could still generate exploitable code, even though it seemed safe and reliable during its training.

Lohrman on Security
JANUARY 14, 2024
What were the top government technology and security blogs in 2023? The metrics tell us what cybersecurity and technology infrastructure topics were most popular.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Troy Hunt
JANUARY 7, 2024
It's another weekly update from the other side of the world with Scott and I in Rome as we continue a bit of downtime before hitting NDC Security in Oslo next week. This week, Scott's sharing details of how he and Joe Tiedman registered a domain Capelli Sport let lapse and now have their JavaScript running on the websites shopping cart page (check your browser console after loading that link) 😲 That's not the crazy bit though, the crazy bit is the months they've spent

Krebs on Security
JANUARY 17, 2024
The rapper and social media personality Punchmade Dev is perhaps best known for his flashy videos singing the praises of a cybercrime lifestyle. With memorable hits such as “Internet Swiping” and “Million Dollar Criminal” earning millions of views, Punchmade has leveraged his considerable following to peddle tutorials on how to commit financial crimes online.

Joseph Steinberg
JANUARY 30, 2024
Embark on a journey of thought leadership into the dynamic realm of cybersecurity, and be part of the conversation and collective effort to shape the future of the industry, by joining the inaugural webinar of Coro’s new series, Cybersphere. Taking place on Thursday, February 1st, 2024 1:00 PM US Eastern Daylight Savings Time (10:00 AM US Pacific = 5:00 PM UTC/GMT), Securing Tomorrow: Cybersecurity Review 2023 & Forecasting 2024 Threats , will be a thought-provoking session that will f

The Last Watchdog
JANUARY 9, 2024
Augmented reality (AR) and virtual reality (VR) technologies provide intriguing opportunities for immersive and interactive experiences in cybersecurity training. Related: GenAI’ impact on DevSecOps Here’s how these technologies can bridge learning gaps in cybersecurity awareness and enhance the overall training experience. AR and VR technologies can create distinct immersive experiences by merging digital reality with the physical world.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Schneier on Security
JANUARY 26, 2024
For most of history, communicating with a computer has not been like communicating with a person. In their earliest years, computers required carefully constructed instructions, delivered through punch cards; then came a command-line interface, followed by menus and options and text boxes. If you wanted results, you needed to learn the computer’s language.

Lohrman on Security
JANUARY 8, 2024
With the modern Internet, it’s easier than ever before to learn from, imitate and even plagiarize other people’s work. So how will new generative AI tools change our media landscape in 2024 and beyond?

Troy Hunt
JANUARY 20, 2024
They're an odd thing, credential lists. Whether they're from a stealer as in this week's Naz.API incident, or just aggregated from multiple data breaches (which is also in Naz.API), I inevitably get some backlash after loading them: "this doesn't tell me anything useful, why are you loading this?!" The answer is easy: because that's what the vast majority of people want me to do: If I have a MASSIVE spam list full of personal data being sold to spammers, should I

Krebs on Security
JANUARY 25, 2024
Google continues to struggle with cybercriminals running malicious ads on its search platform to trick people into downloading booby-trapped copies of popular free software applications. The malicious ads, which appear above organic search results and often precede links to legitimate sources of the same software, can make searching for software on Google a dicey affair.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Joseph Steinberg
JANUARY 19, 2024
Several hours ago , I received a phone call; the caller ID displayed the accurate name and phone number of my local utility company. As our area has, at times, suffered from power disruptions during winter storms, and we had winter weather yesterday and are expecting more tomorrow, I answered the call to see if the utility was advising of some repair that could impact service.

The Last Watchdog
JANUARY 2, 2024
In today’s digital landscape, organizations face numerous challenges when it comes to mitigating cyber risks. Related: How AI is transforming DevOps The constant evolution of technology, increased connectivity, and sophisticated cyber threats pose significant challenges to organizations of all sizes and industries. Here are some of the key challenges that organizations encounter in their efforts to mitigate cyber risks in the current environment.

Schneier on Security
JANUARY 2, 2024
TikTok seems to be skewing things in the interests of the Chinese Communist Party. (This is a serious analysis, and the methodology looks sound.) Conclusion: Substantial Differences in Hashtag Ratios Raise Concerns about TikTok’s Impartiality Given the research above, we assess a strong possibility that content on TikTok is either amplified or suppressed based on its alignment with the interests of the Chinese Government.

Tech Republic Security
JANUARY 29, 2024
New research details the possible effects of ransomware attacks on businesses and staff, society, the economy and national security, highlighting that its impact on mental and physical health is often overlooked.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Troy Hunt
JANUARY 27, 2024
I spent longer than I expected talking about Trello this week, in part because I don't feel the narrative they presented properly acknowledges their responsibility for the incident and in part because I think the impact of scraping in general is misunderstood. I suspect many of us are prone to looking at this in a very binary fashion: if the data is publicly accessible anyway, scraping it poses no risk.
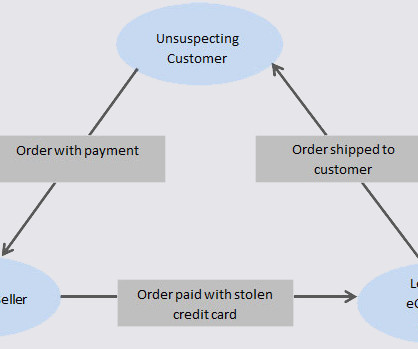
Krebs on Security
JANUARY 19, 2024
A Canadian man who says he's been falsely charged with orchestrating a complex e-commerce scam is seeking to clear his name.

Joseph Steinberg
JANUARY 18, 2024
Securing Success: The Crucial Role of a Cybersecurity Specialist in a Growing Business Human society is increasingly dependent on computer systems and the data housed and utilized within IT (information technology) infrastructure. While technological advances have, in some ways, allowed humans to enjoy an unprecedented quality of life, they also create significant risks.

Lohrman on Security
JANUARY 28, 2024
Every January, NASCIO and PTI release their forecasts for the coming year based on what government leaders are saying. So what’s coming in 2024? Here’s a roundup of top CIO priorities.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
Let's personalize your content