Booking.com Phishers May Leave You With Reservations
Krebs on Security
NOVEMBER 1, 2024
We’ll also explore an array of cybercrime services aimed at phishers who target hotels that rely on the world’s most visited travel website. Booking.com did not respond to questions about that, and its current account security advice urges customers to enable 2FA. A full, defanged list of domains is available here.


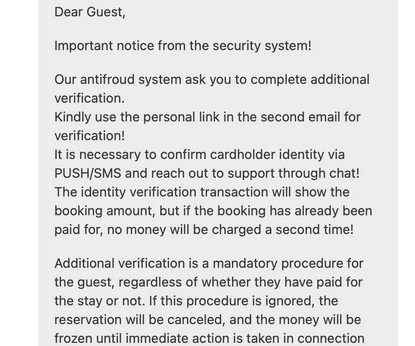









Let's personalize your content