SANS Outlines Critical Infrastructure Security Steps as Russia, U.S. Trade Cyberthreats
eSecurity Planet
FEBRUARY 25, 2022
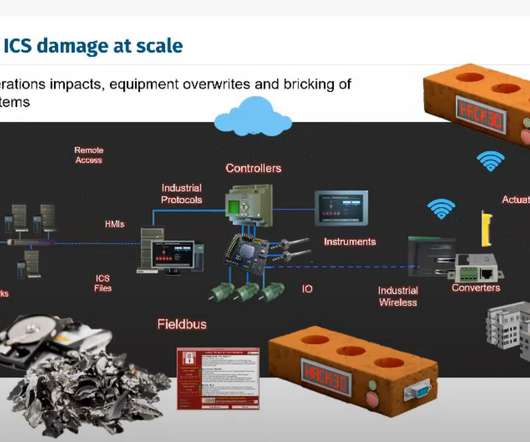
Williams urged viewers to focus on the basics, like phishing , passwords and patching /updating, as those are still the entry point of many attacks. Inventory B2B VPNs and block all high-risk protocols (see slide below). Inventory B2B VPNs and block all high-risk protocols (see slide below). Plan for rapid containment.








Let's personalize your content