GUEST ESSAY: How stricter data privacy laws have redefined the ‘filing’ of our personal data
The Last Watchdog
NOVEMBER 4, 2021
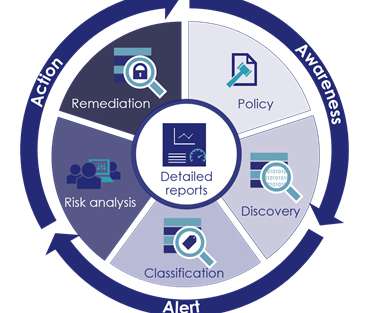
Companies are also often dealing with numerous kinds of storage, from relational databases to schema-less databases, to giant data dumps of unstructured data in, say, Amazon S3 data storage buckets. It’s no wonder that the global GDPR services market is expected to reach $4.4 billion by 2027. Less can be more.













Let's personalize your content