Inside the Massive Alleged AT&T Data Breach
Troy Hunt
MARCH 18, 2024
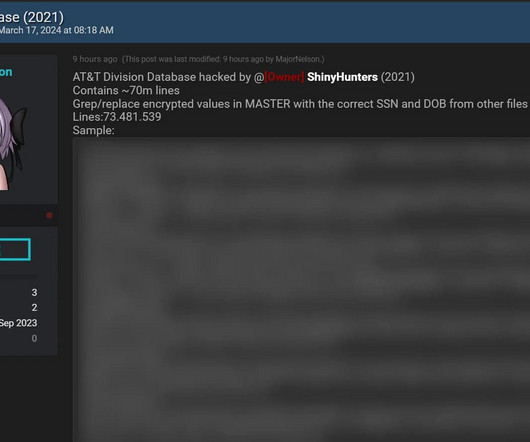
The linked article talks about the author verifying the data with various people he knows, as well as other well-known infosec identities verifying its accuracy. Per the linked story, social security numbers and dates of birth exist on most rows of the data in encrypted format, but two supplemental files expose these in plain text.











Let's personalize your content