North Korea-linked Lazarus APT targets defense industry with ThreatNeedle backdoor
Security Affairs
FEBRUARY 25, 2021
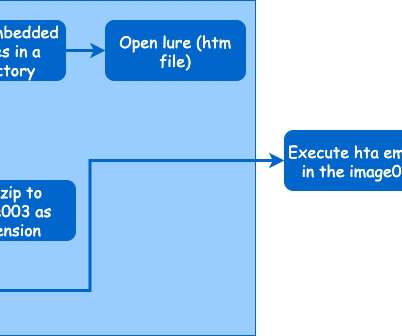
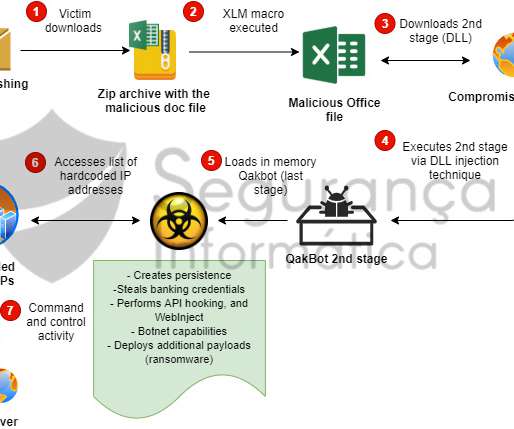
The attack chain starts with COVID19-themed spear-phishing messages that contain either a malicious Word attachment or a link to one hosted on company servers. . Attackers employed a custom tunneling tool to achieve this, it forwards client traffic to the server, the malware encrypts the traffic using trivial binary encryption.











Let's personalize your content