DDoS attacks in Q2 2021
SecureList
JULY 28, 2021
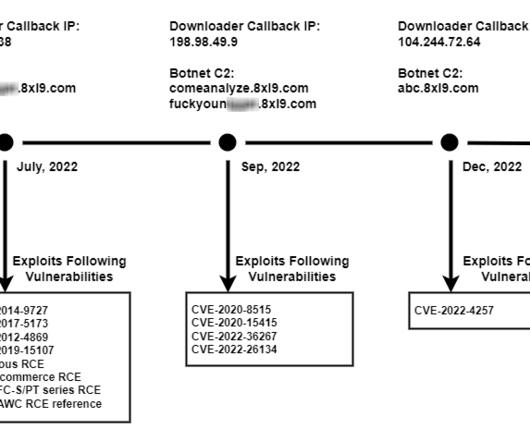
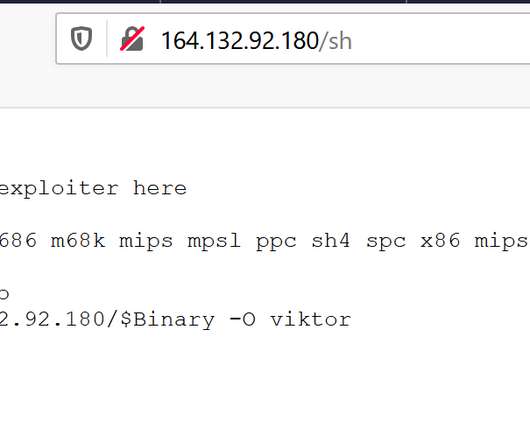
For example, April saw the active distribution of a new DDoS botnet called Simps — the name under which it introduced itself to owners of infected devices. The malware creators promoted their brainchild on a specially set-up YouTube channel and Discord server, where they discussed DDoS attacks.











Let's personalize your content