3 of the Worst Data Breaches in the World That Could Have Been Prevented
Security Affairs
DECEMBER 1, 2022
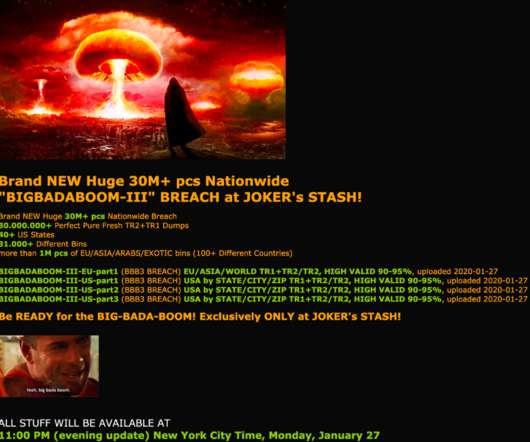
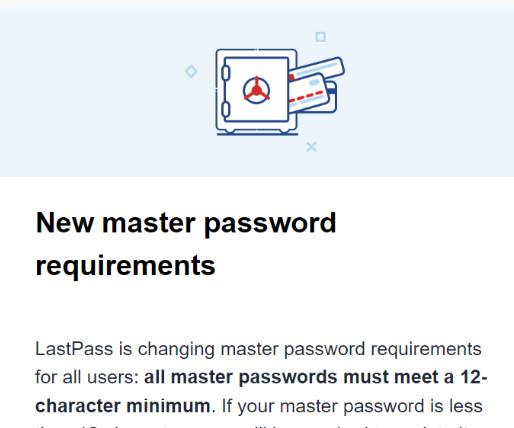
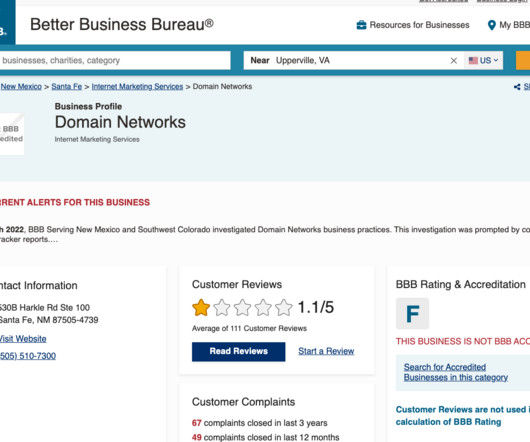
Data breaches can be devastating for organizations, these are 3 of the worst incidents that could have been prevented. Data breaches can be devastating for organizations and even entire countries. Eliminating the risk of a data breach is nearly impossible, but some things can be done to reduce it significantly.


































Let's personalize your content