NCSC warns of a surge in ransomware attacks on education institutions
Security Affairs
SEPTEMBER 20, 2020
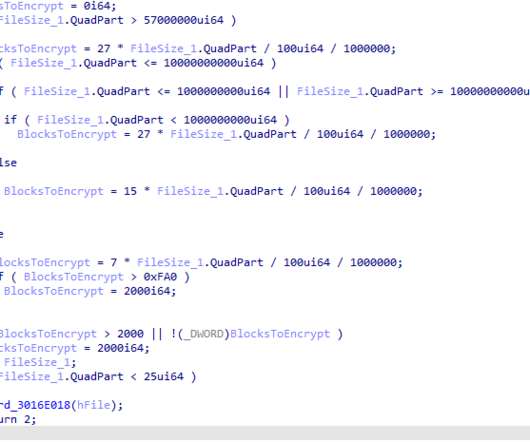
Once gained the foothold in the target network, the attackers will attempt lateral movements to elevate the privileges and search for high-value machines to encrypt (i.e. backup servers, network shares, servers, auditing devices). Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.

















Let's personalize your content