Experts link the Black Basta ransomware operation to FIN7 cybercrime gang
Security Affairs
NOVEMBER 3, 2022
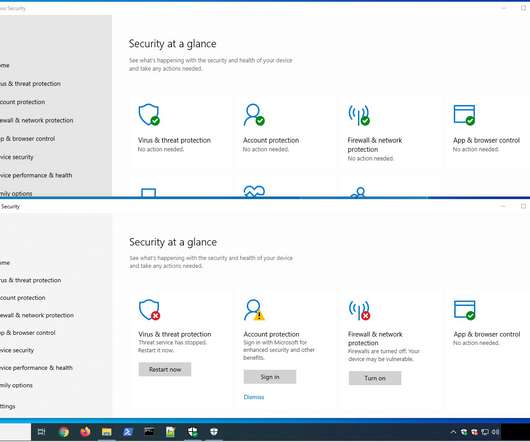
On the other end, FIN7 is a Russian financially motivated group that has been active since at least 2015. It focused on deploying POS malware and launching targeted spear-phishing attacks against organizations worldwide. The threat actors were disabling Windows Defender executing the following scripts: WindowsILUg69ql1.bat











Let's personalize your content