Moobot botnet spreads by exploiting CVE-2021-36260 flaw in Hikvision products
Security Affairs
DECEMBER 8, 2021
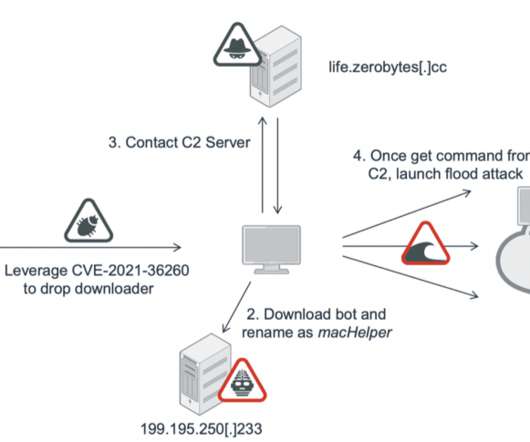
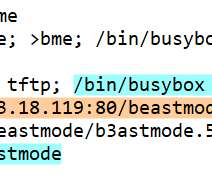
The Mirai -based Moobot botnet is rapidly spreading by exploiting a critical command injection flaw, tracked as CVE-2021-36260 , in the webserver of several Hikvision products. The Moobot was first documented by Palo Alto Unit 42 researchers in February 2021, the recent attacks demonstrated that its authors are enhancing their malware.


















Let's personalize your content