Modernizing Secure Remote Access for a Hybrid Workforce
Duo's Security Blog
MARCH 25, 2022
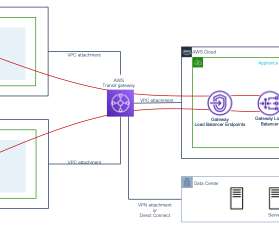
Problem: The Traditional VPN Is No Longer Enough Since the 1990s, virtual private networks (VPNs) have been well-suited for the purpose they were built for – to grant employees temporary access to corporate networks and resources when they weren't logging in from an office.











Let's personalize your content