Google Cybersecurity Action Team Threat Horizons Report #8 Is Out! [Medium Backup]
Security Boulevard
NOVEMBER 3, 2023
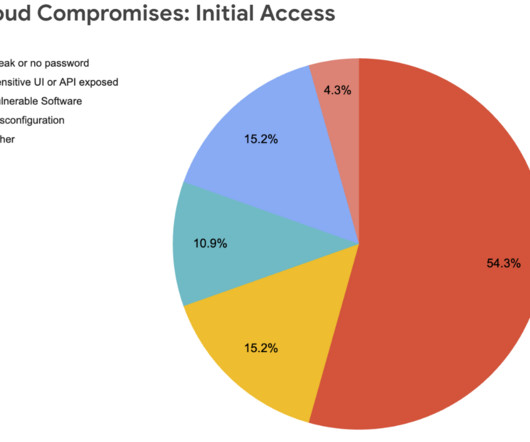
This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our eighth Threat Horizons Report ( full version ) that we just released ( the official blog for #1 report , my unofficial blogs for #2 , #3 , #4 , #5 , #6 and #7 ).










Let's personalize your content