Fake Company Sheds Light on Ransomware Group Tactics
eSecurity Planet
NOVEMBER 4, 2021
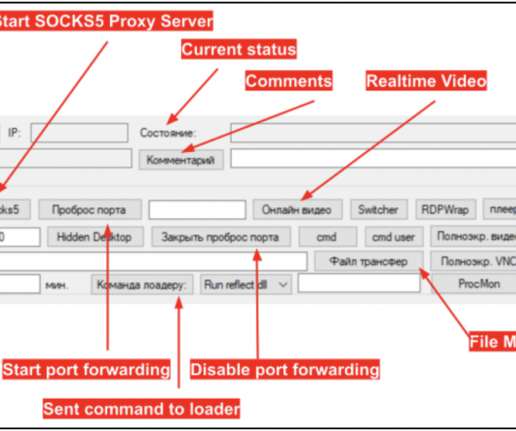
The goal was to make the victims run illegal penetration tests and ransomware attacks unwittingly. They targeted specific profiles such as system administrators who know how to map corporate networks, locate backups and identify users within a system, which are critical steps in ransomware attacks. starting salary.














Let's personalize your content