Experts spotted Syslogk, a Linux rootkit under development
Security Affairs
JUNE 14, 2022
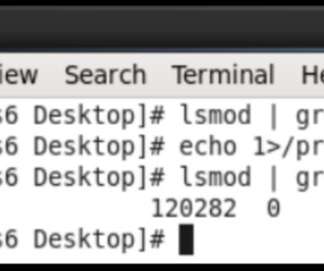
Researchers from antivirus firm Avast spotted a new Linux rootkit, dubbed ‘Syslogk,’ that uses specially crafted “magic packets” to activate a dormant backdoor on the device. Experts spotted a new Linux rootkit, dubbed ‘Syslogk,’ that uses specially crafted “magic packets” to activate a dormant backdoor on the device.










Let's personalize your content