Hackers are using Zerologon exploits in attacks in the wild
Security Affairs
SEPTEMBER 24, 2020
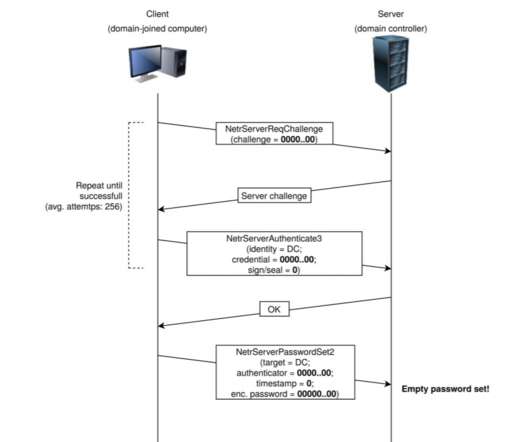
— Microsoft Security Intelligence (@MsftSecIntel) September 24, 2020. We strongly recommend customers to immediately apply security updates for CVE-2020-1472. We strongly recommend customers to immediately apply security updates for CVE-2020-1472.












Let's personalize your content