CERT-UA warns of cyber espionage against the Ukrainian defense industry using Dark Crystal RAT
Security Affairs
MARCH 20, 2025
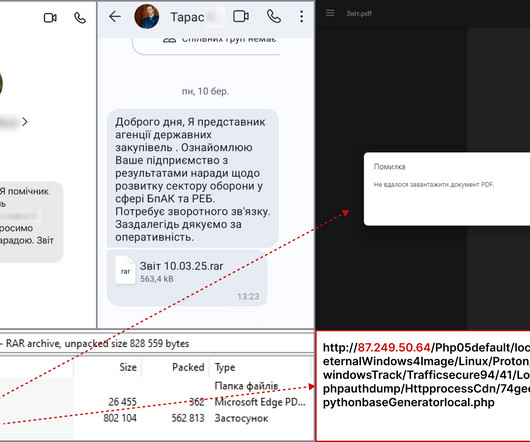
The Computer Emergency Response Team of Ukraine (CERT-UA) uncovered a new cyber espionage campaign targeting employees of defense-industrial complex enterprises and representatives of the Defense Forces of Ukraine with Dark Crystal RAT. CERT-UA published Indicators of Compromise (IoCs) for the ongoing campaign.













Let's personalize your content