Multiple DDoS botnets were observed targeting Zyxel devices
Security Affairs
JULY 22, 2023
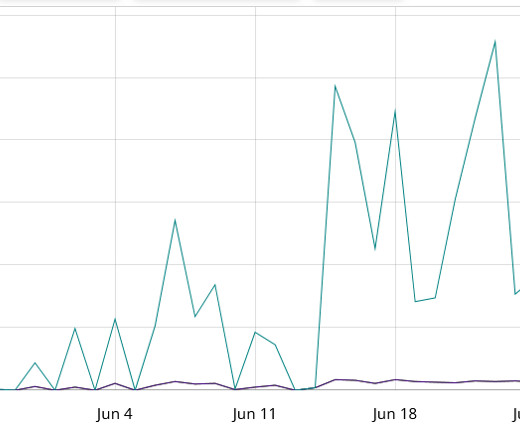
Fortinet FortiGuard Labs researchers warned of multiple DDoS botnets exploiting a vulnerability impacting multiple Zyxel firewalls. The cause of the vulnerability is the improper error message handling in Zyxel ZyWALL/USG series firmware versions 4.60 through 4.73, VPN series firmware versions 4.60 through 5.35. through 5.35.
















Let's personalize your content