Would You Have Fallen for This Phone Scam?
Krebs on Security
APRIL 28, 2020
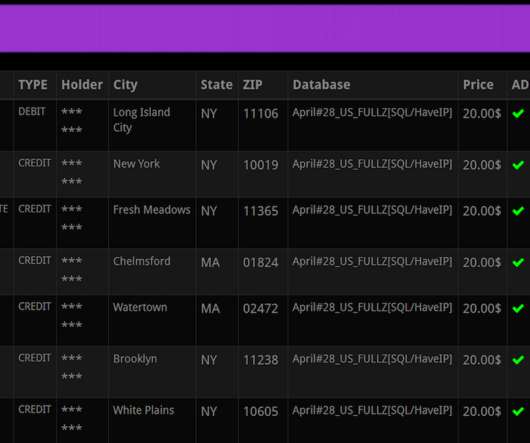
You may have heard that today’s phone fraudsters like to use use caller ID spoofing services to make their scam calls seem more believable. Sure enough, he said, as long as he was calling from the number on file for his account, the automated system let him review recent transactions without any further authentication.













Let's personalize your content