SMS Security & Privacy Gaps Make It Clear Users Need a Messaging Upgrade
Google Security
SEPTEMBER 27, 2023
People still use and rely on trillions of SMS texts each year to exchange messages with friends, share family photos, and copy two-factor authentication codes to access sensitive data in their bank accounts. Like any forty-year-old technology, SMS is antiquated compared to its modern counterparts.

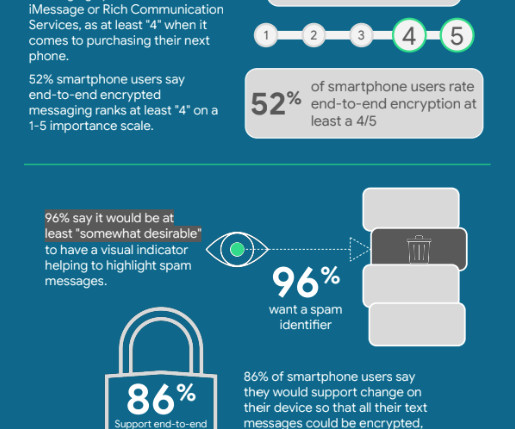









Let's personalize your content