How Secure Shell (SSH) Keys Work
Security Boulevard
AUGUST 5, 2022
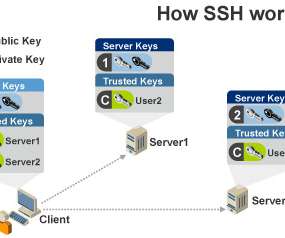
But SSH protocol version 1 is limited in its support of message authorization codes, compression algorithms, and the algorithms necessary for key exchanges. David Bisson. As Justin Elingwood of DigitalOcean explains , SSH encrypts data exchanged between two parties using a client-server model. Related blogs.













Let's personalize your content