A Day in the Life of a Prolific Voice Phishing Crew
Krebs on Security
JANUARY 7, 2025
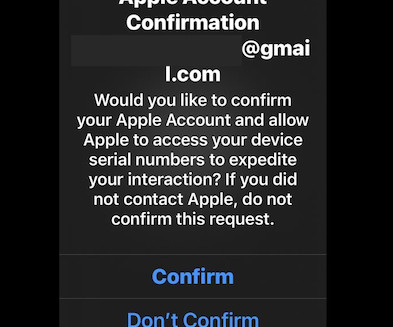
Each participant in the call has a specific role, including: -The Caller: The person speaking and trying to social engineer the target. A tutorial shared by Stotle titled “Social Engineering Script” includes a number of tips for scam callers that can help establish trust or a rapport with their prey.













Let's personalize your content