Ransomware Gangs and the Name Game Distraction
Krebs on Security
AUGUST 5, 2021
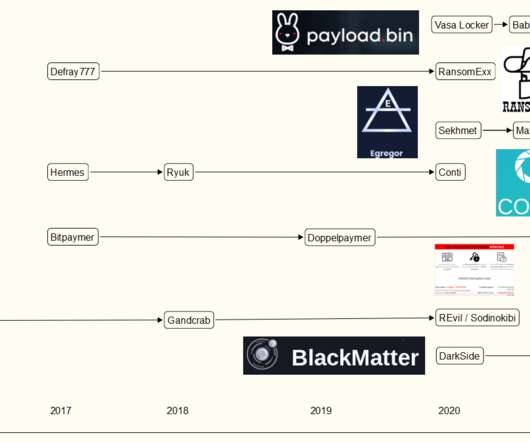
Reinvention is a basic survival skill in the cybercrime business. Among the oldest tricks in the book is to fake one’s demise or retirement and invent a new identity. REvil’s last big victim was Kaseya , a Miami-based company whose products help system administrators manage large networks remotely. Image: FBI.










Let's personalize your content