Cybersecurity Snapshot: CSA Outlines Data Security Challenges and Best Practices, While ISACA Offers Tips To Retain IT Pros
Security Boulevard
MARCH 7, 2025
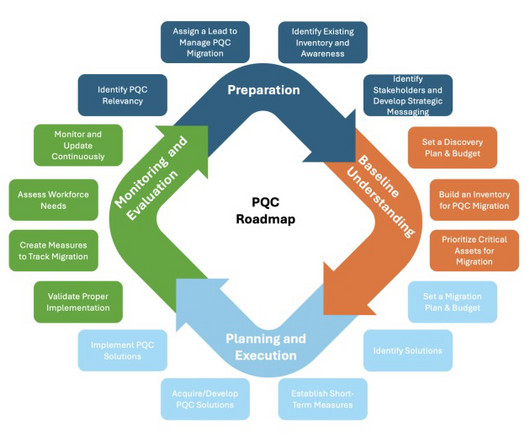
Check out best practices for shoring up data security and reducing cyber risk. 1 - CSA: How to boost data security and reduce cyber risk Risk assessment gaps. 1 - CSA: How to boost data security and reduce cyber risk Risk assessment gaps. Plus, get tips on how to improve job satisfaction among tech staff.

















Let's personalize your content