Cybersecurity awareness: Train your employees and reduce cyber threats
IT Security Guru
DECEMBER 1, 2022
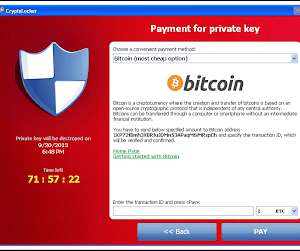
It teaches people about cyber threats and dangers, safety precautions, HIPAA and PCI DSS requirements, and several privacy regulations. These training programs imitate cyberattacks and educate people about existing malware. In other words, what we have to do is to manage human risk in the most competent manner.













Let's personalize your content