New CACTUS ransomware appeared in the threat landscape
Security Affairs
MAY 9, 2023
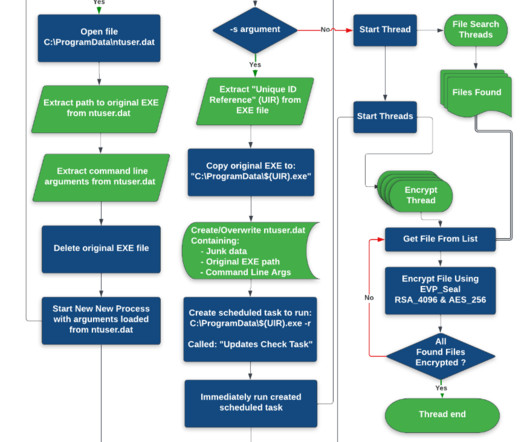
Researchers warn of a new ransomware family called CACTUS that exploits known vulnerabilities in VPN appliances to gain initial access to victims’ networks. The new ransomware operation has been active since March 2023, despite the threat actors use a double-extortion model, their data leak site has yet to be discovered.















Let's personalize your content