Cooking Intelligent Detections from Threat Intelligence (Part 6)
Anton on Security
DECEMBER 1, 2023
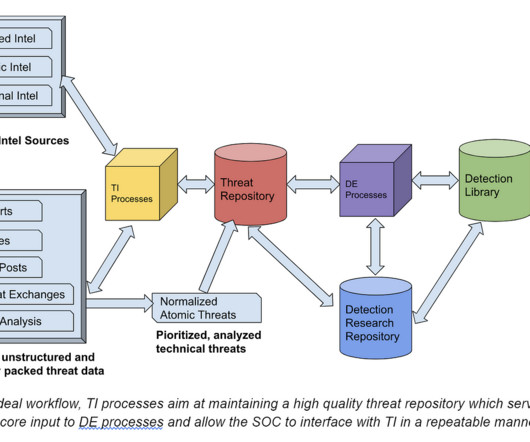
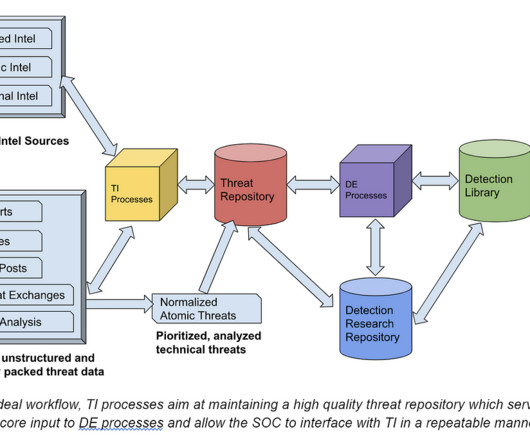
While some instances of TI might be driven by research interests or executive curiosity, its primary purpose lies in empowering cyber defenders with usable insights. In essence, TI plays a pivotal role in bridging the gap between understanding and action in the cybersecurity realm.








Let's personalize your content