Encryption: How It Works, Types, and the Quantum Future
eSecurity Planet
MAY 25, 2022
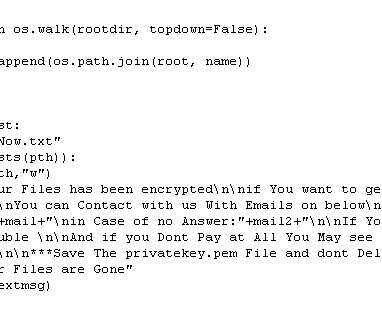
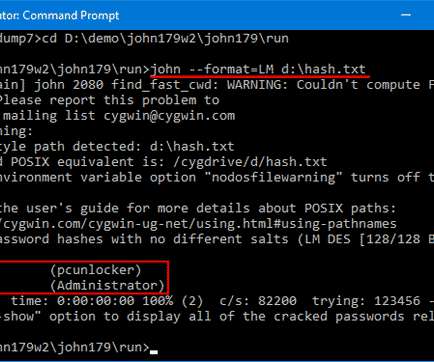
Encryption and the development of cryptography have been a cornerstone of IT security for decades and remain critical for data protection against evolving threats. While cryptology is thousands of years old, modern cryptography took off in the 1970s with the help of the Diffie-Hellman-Merkle and RSA encryption algorithms.






















Let's personalize your content