Threat Report Portugal: Q4 2021
Security Affairs
FEBRUARY 20, 2022
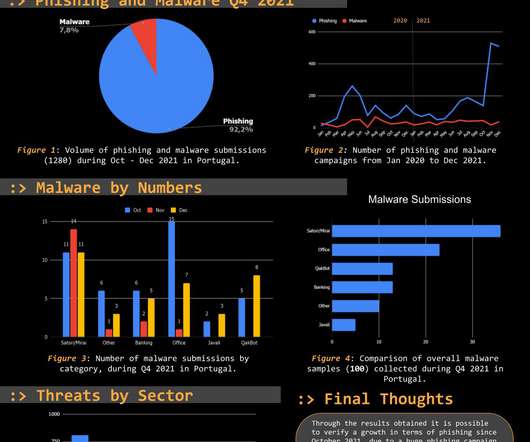
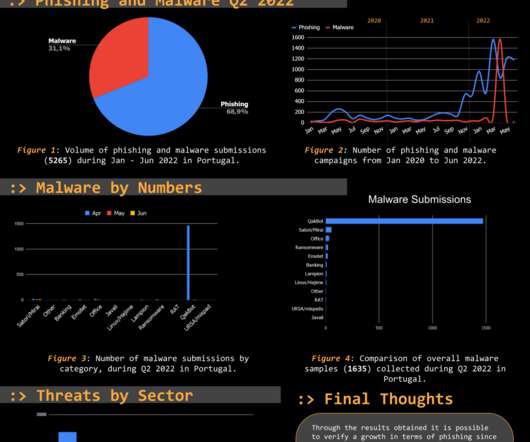
The Threat Report Portugal: Q4 2021 compiles data collected on the malicious campaigns that occurred from July to September, Q4, of 2021. The Portuguese Abuse Open Feed 0xSI_f33d is an open sharing database with the ability to collect indicators from multiple sources, developed and maintained by Segurança-Informática.











Let's personalize your content