Defeating Malvertising-Based Phishing Attacks
Security Boulevard
MARCH 3, 2023
Webinar: Emulating Threat Actors in OT Networks - DNS Tunneling Mar 23 @ 10:00 AM (PST) While it is possible to write signatures for malware of this type after analysis is completed, it takes time — time during which the malware is able to evade even the most advanced EDRs while it goes about its business. Next-gen protective DNS.


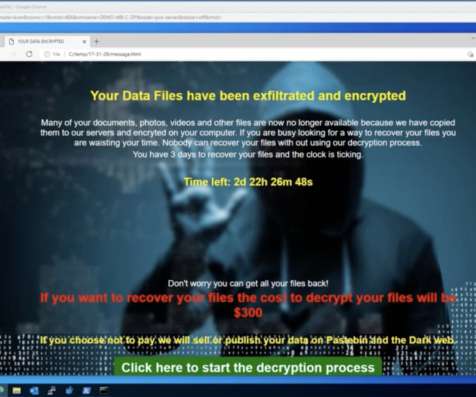








Let's personalize your content