Operation Endgame
Troy Hunt
MAY 29, 2024
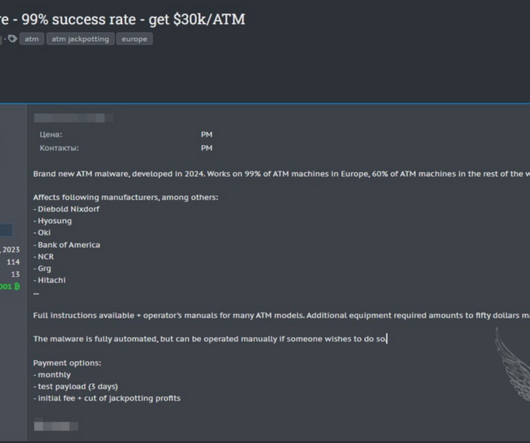
Today we loaded 16.5M email addresses and 13.5M unique passwords provided by law enforcement agencies into Have I Been Pwned (HIBP) following botnet takedowns in a campaign they've coined Operation Endgame. That link provides an excellent over so start there then come back to this blog post which adds some insight into the data and explains how HIBP fits into the picture.

























Let's personalize your content