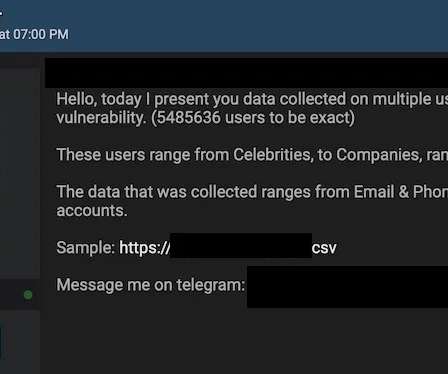
Data from 5.4M Twitter users obtained from multiple threat actors and combined with data from other breaches
Security Affairs
NOVEMBER 26, 2022
The massive data breach suffered by Twitter that exposed emails and phone numbers of its customers may have impacted more than five million users. At the end of July, a threat actor leaked data of 5.4 million Twitter accounts that were obtained by exploiting a now-fixed vulnerability in the popular social media platform. The threat actor offered for sale the stolen data on the popular hacking forum Breached Forums.










Let's personalize your content